If you are paying close attention to the news, you must already know that cybercrime has become a very usual occurrence since the beginning of this decade. Not only does this pose a huge threat towards individual security and privacy, multi-million-dollar companies, banks and governments could face meltdowns if their data is compromised. We don’t see lone hackers who are testing out their skills on the internet anymore. Hacking has become an organized crime system where a bunch of skilled computer specialists take down anything from websites to servers.
So, cybercrime is a huge and impending threat. But, how do you defend against this?
That’s where cybersecurity comes in. Let’s now take a few minutes to understand what cybersecurity is and how it can help protect the privacy of individuals and international organizations.
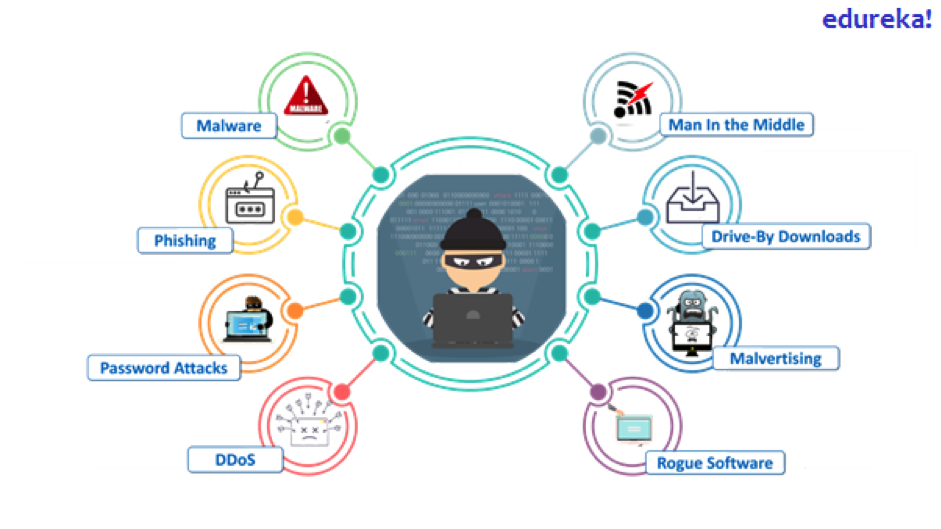
Before we define cybersecurity, let’s look at a few of the most dangerous cyberattacks.
Cyberattacks
These were just a few of the most well-known types of cyberattacks. Newer and more dangerous kinds come out almost daily. This makes cybersecurity one of the most dynamic technology fields as it needs to adapt to different threats every day.
Cybersecurity Defined
Cybersecurity is, at its core, a set of techniques employed to protect the integrity of networks, programs and data from unauthorized access, attack or damage.
There are three main aspects that cybersecurity deals with and tries to protect the digital data from:
- Unauthorized Access
- Unauthorized Deletion
- Unauthorized Modification
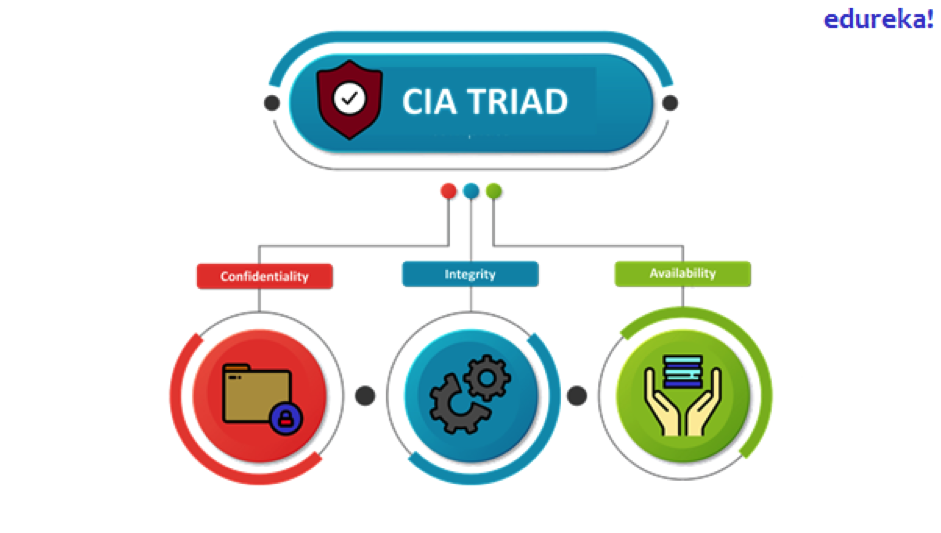
For cybersecurity professionals, these three terms are shortened and called the CIA Triad. CIA stands for Confidentiality, Integrity and Availability. Some people also refer to these terms as the three pillars of cybersecurity. Most companies and organizations build their security policies on top of these pillars.
Let’s discuss what these pillars stand for, individually.
Confidentiality
Confidentiality simply put is keeping you and your client’s data just between the two of you and protecting against unauthorized access from a third-party.
Integrity
The idea of ensuring the quality and accuracy of data and safeguarding it against any unauthorized modification is called integrity.
Availability
The ability for an authorized user to access data from a specified location in the right format is referred to as availability.
Blueprint of Cybersecurity
Just like any other technology, cybersecurity can be implemented in many ways following a set of guidelines. These guidelines, just like everything else we’ve seen come in a group of three.
- Identify
- Analyze and Evaluate
- Treat
As evident from above, the first step is to recognize what the issue or threat is. After the required data is collected from the problem, it is analyzed and evaluated to isolate all the compromised data and information. Further, vulnerabilities in the threat need to be discovered. Finally, the best possible course of action is taken to treat the issue and restore confidentiality, integrity and availability of the data.
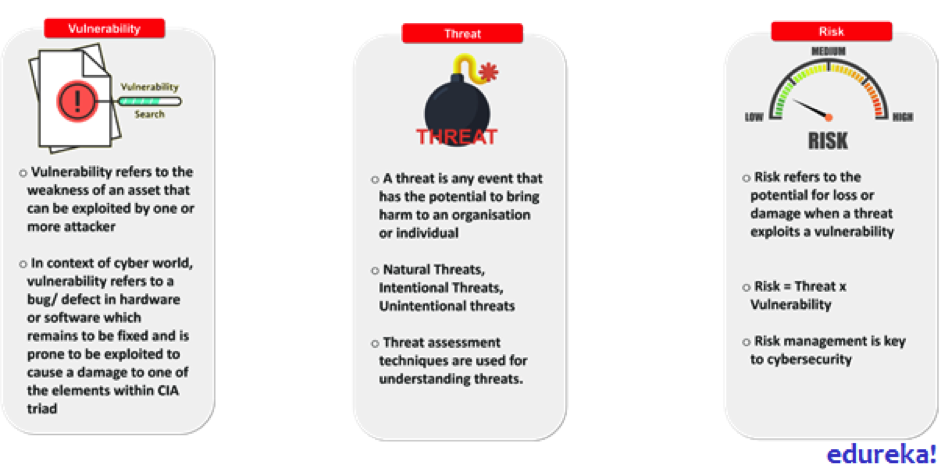
These three guidelines have three other factors that are to be considered while implementing. They are:
- Vulnerability
- Threat
- Risk
Cybersecurity is one of the most important technological fields in the market right now. Furthermore, there is a huge deficiency of skilled professionals in the market which means that companies and organizations are offering great incentives to anyone who joins them in this field.
So, if you are looking for a career that is dynamic, high paying and interesting, why not learn Cybersecurity and get into your dream role?
Thanks for reading this article. If you're new here, why don't you subscribe for regular updates via RSS feed or via email. You can also subscribe by following @techsling on Twitter or becoming our fan on Facebook. Thanks for visiting!